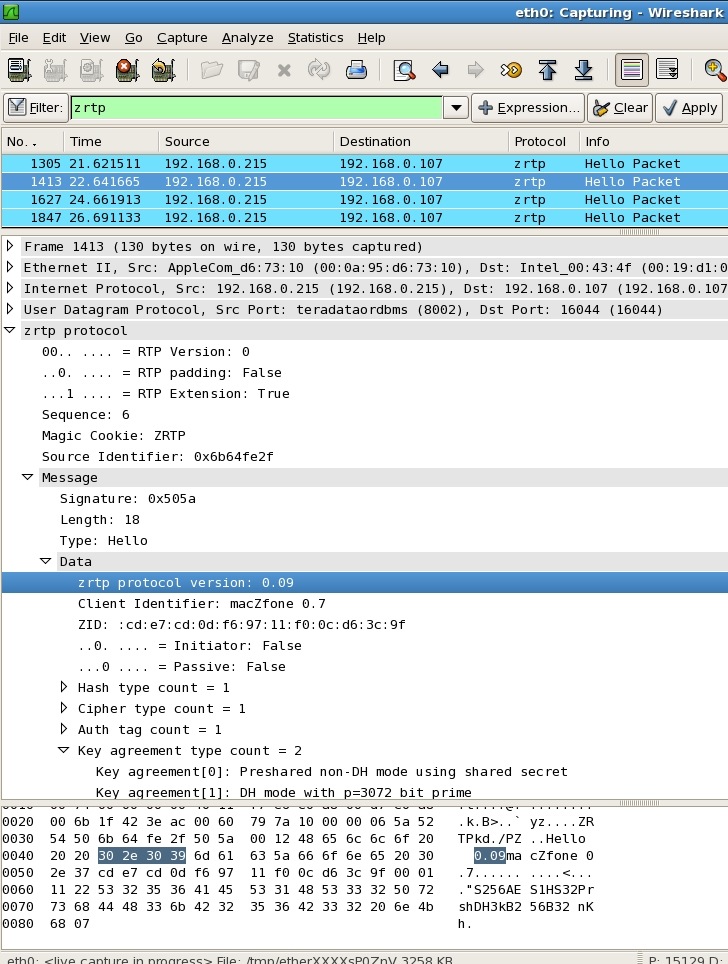
Wireshark (Ethereal) ZRTP packet dissector
VoIP developers may want to use the popular open source Wireshark protocol analyzer, formerly known as Ethereal, to inspect ZRTP packets as part of their development of VoIP applications that use the ZRTP protocol. To this end, Sagar Pai has developed a nifty ZRTP packet dissector for Wireshark. This has become a built-in feature of Wireshark (version 1.2.0 or later). It parses packets for ZRTP protocol versions 0.85 through 1.1.
Using Wireshark on the same machine as Zfone
If you want to use Wireshark to capture Zfone encrypted VoIP traffic on the same machine that Zfone is running on, you cannot do it on Windows. This is because on Windows, the Zfone device driver is closer to the network adapter than the Wireshark device driver. This means Wireshark captures only unencrypted IP traffic. Zfone has already decrypted incoming packets before Wireshark can see them, and Zfone only encrypts outgoing packets after they have passed through Wireshark. This problem only exists on Windows.
If you need to capture encrypted packets from a Windows machine running Zfone, you must run Wireshark on a separate machine between the two parties.
The ZRTP RFC and libZRTP SDK for developers
ZRTP packet formats are defined in RFC 6189. We also have a software development kit to help you implement ZRTP in your VoIP application. Click here to see the Zfone libZRTP SDK documentation. For general information about the ZRTP SDK, including licensing information, see the Zfone libZRTP SDK page.
Screen shot of Wireshark ZRTP packet dissector
Here's what it looks like, inspecting a typical ZRTP packet: